Description
James Bonderman has retrieved some files from an enemy agent’s system. As one of R Branch’s support engineers, Bonderman is trusting you to find any information relevant to his investigation. R has sent you a checklist of what he wants you to find. That should be easy for an agent such as yourself.
nc misc.chal.csaw.io 5015
Author: Regulus915ap
Challenge Files: https://drive.google.com/file/d/1Xyy__6d_bV3E5mRvF719i2nHJ0PHh7RZ/view?usp=sharing
Tools
- RegistryExplorer
- RegRipper
- USB Forensic Tracker
- Windows Registry analysis cheat sheet
- DCode™ – Timestamp Decoder
- USBDeview
- WinProdKeyFinder
Walkthrough
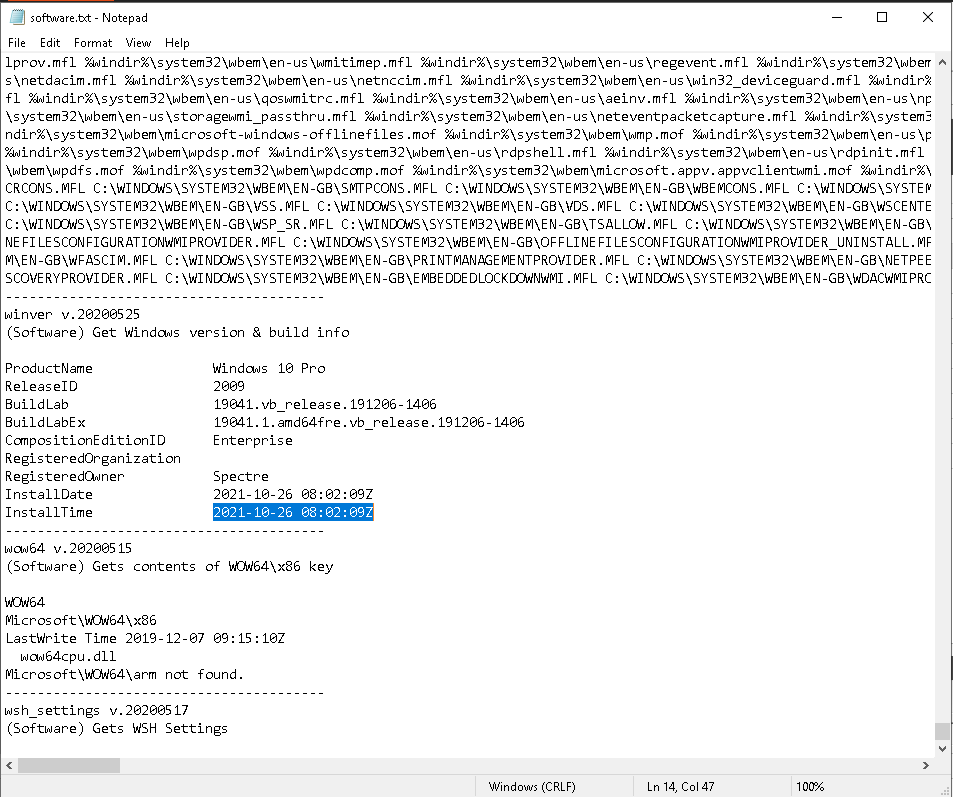
We were given a server to connect to, asking for data to extract from the registry hives (SAM, SYSTEM, SOFTWARE). We will start our analysis by running regrip to scan the registry hives then load them to registry explorer.
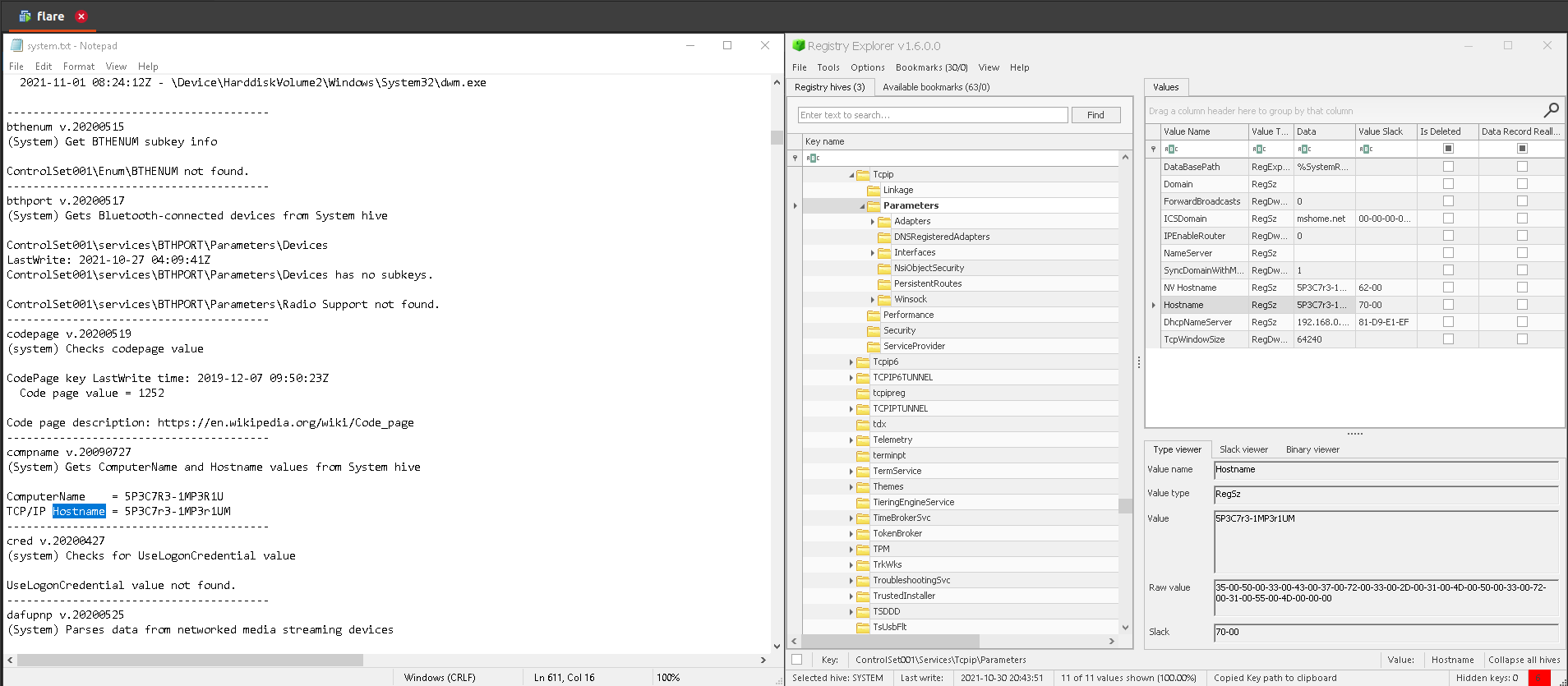
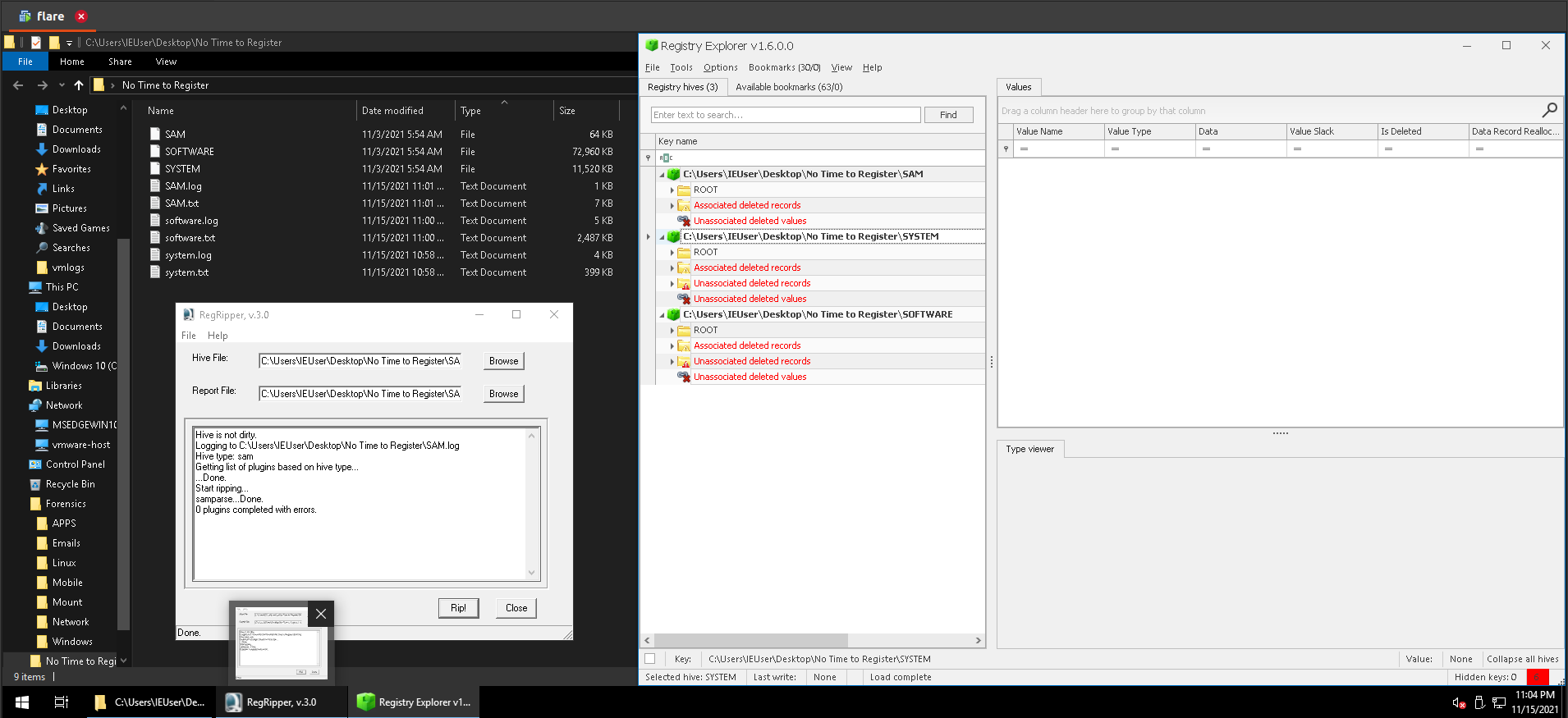 1.Hostname of the machine
1.Hostname of the machine
a. Registry Explorer: Check Tcpip in the bookmarks menu or browse to SYSTEM:ControlSet001\Services\Tcpip\Parameters.
b. RegRipper: Search for ‘Hostname’ in the system hive report.txt generated by RegRipper.
Answer: 5P3C7r3-1MP3r1UM
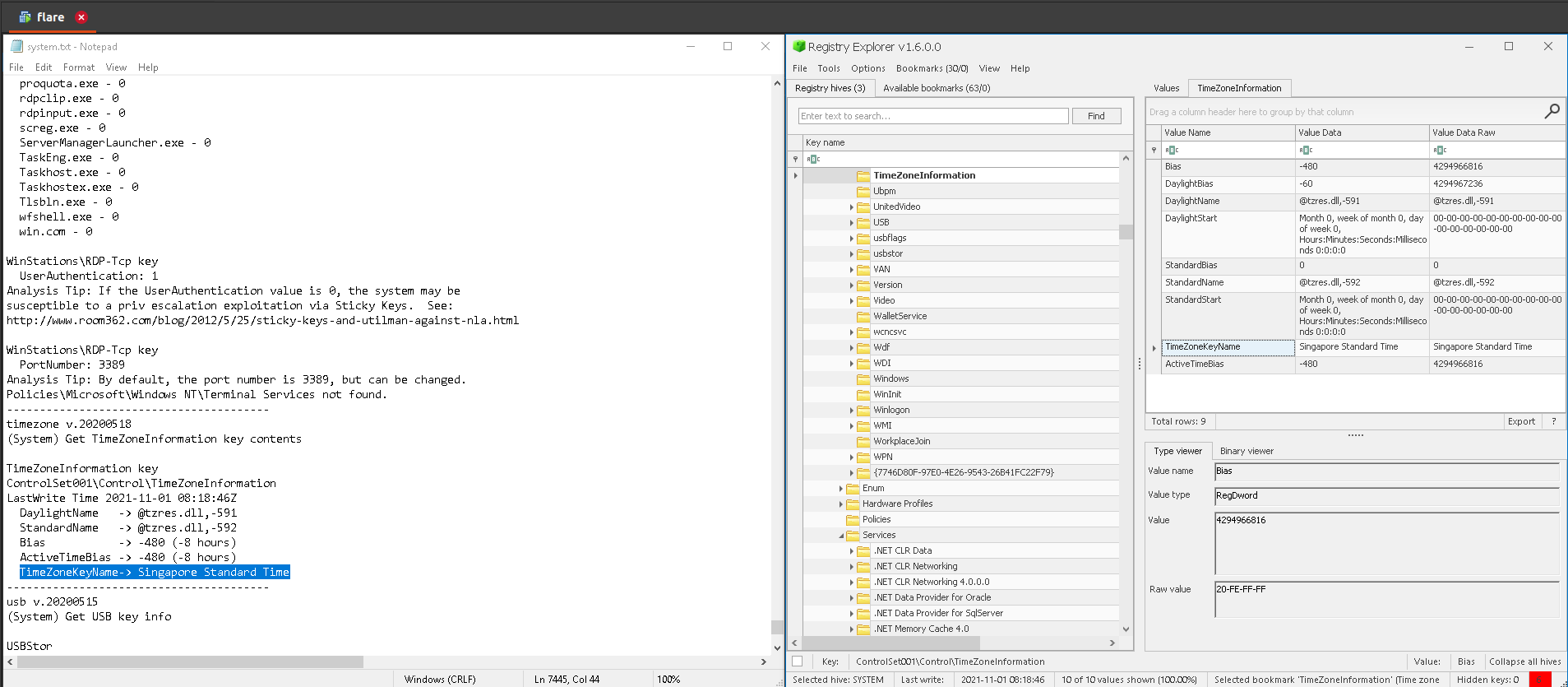
 2.Region the machine belong to
2.Region the machine belong to
a. Registry Explorer: Registry Explorer: check Timezoneinformation in the bookmarks menu or browse to SYSTEM:ControlSet001\Control\TimeZoneInformation.
b. RegRipper: Search for ‘timezone’ in the system hive report.txt generated by RegRipper.
Answer: Singapore
 3.User registered on the machine
3.User registered on the machine
a. Registry Explorer: check Users in the bookmarks menu or browse to SAM:SAM\Domains\Account\Users.
b. RegRipper: Check registered users in the sam hive report.txt generated by RegRipper.
Answer: Spectre
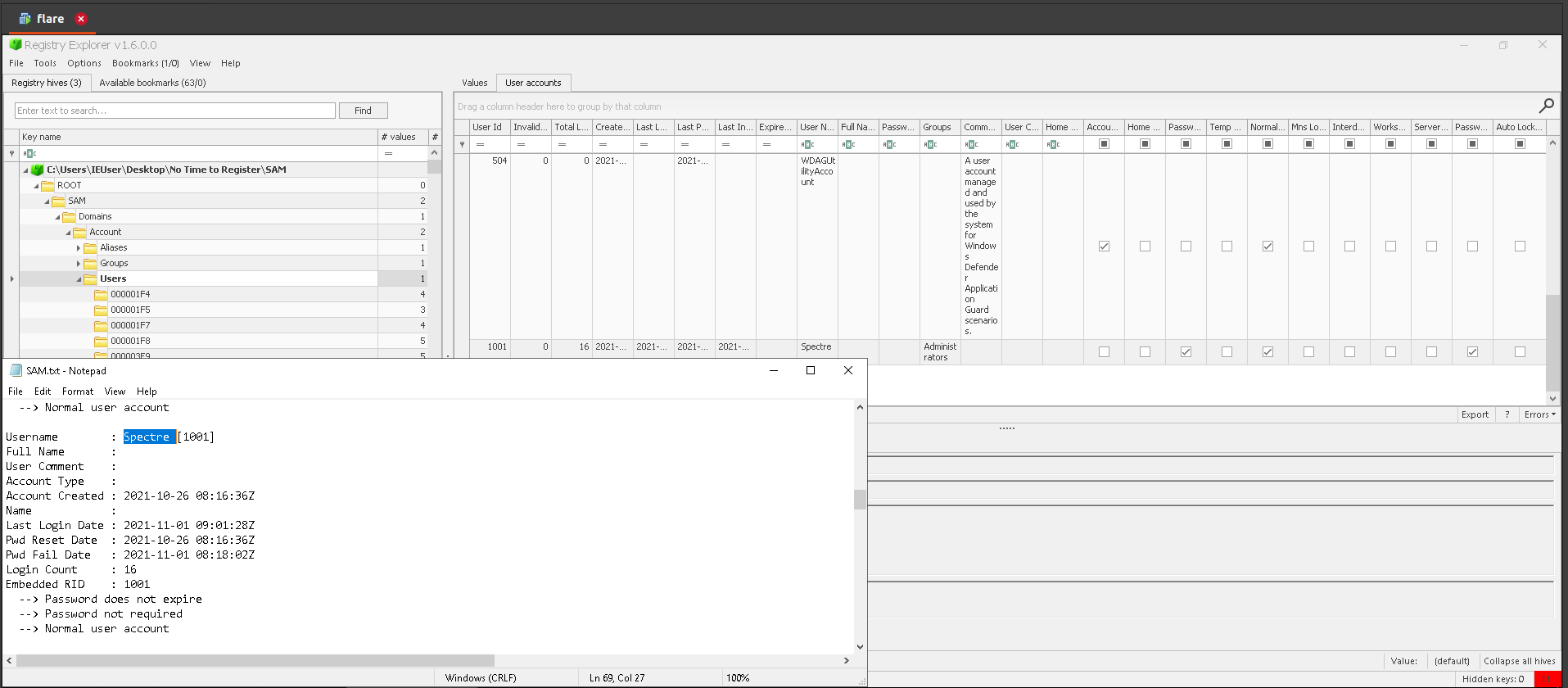 4.GUID of the user from 3
4.GUID of the user from 3
a. Registry Explorer: browse to SOFTWARE:Microsoft\Windows NT\CurrentVersion\ProfileList. Check the keys listed under ProfileList.
b. RegRipper: Search for ‘spectre’ in the software hive report.txt generated by RegRipper.
Answer: S-1-5-21-4228526091-1870561526-3973218081-1001
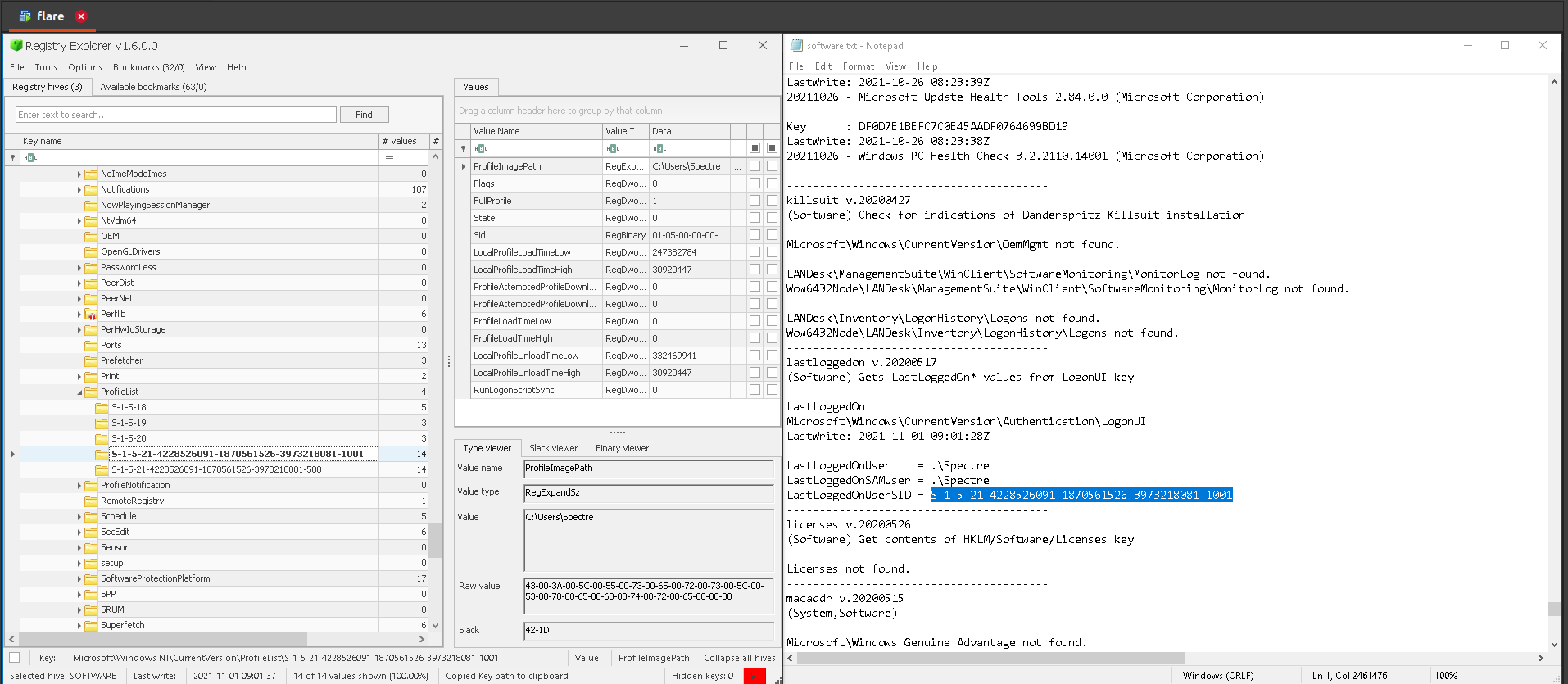 5.Last login time of user from 3 using the timezone found in 2. (Use format HH:MM:SS MM/DD/YYYY)
5.Last login time of user from 3 using the timezone found in 2. (Use format HH:MM:SS MM/DD/YYYY)
a. Registry Explorer: check Users in the bookmarks menu or browse to SAM:SAM\Domains\Account\Users.
b. RegRipper: Check spectre in the sam hive report.txt generated by RegRipper.
Answer: 2021-11-01 09:01:28Z
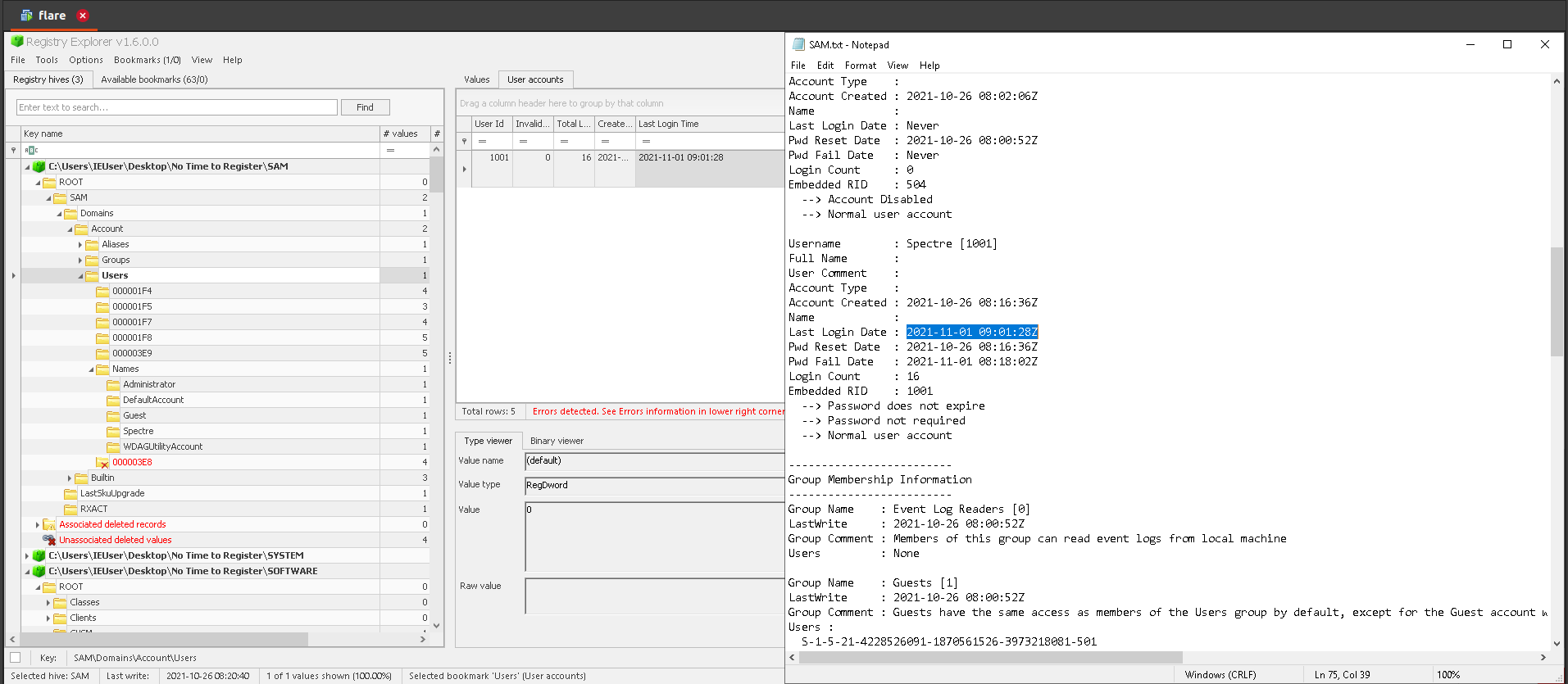 6.Other accounts enabled on the machine
6.Other accounts enabled on the machine
a. Registry Explorer: check Users in the bookmarks menu or browse to SAM:SAM\Domains\Account\Users. Check accounts which has last login date.
b. RegRipper: Check users in the sam hive report.txt generated by RegRipper.
Answer: Administrator
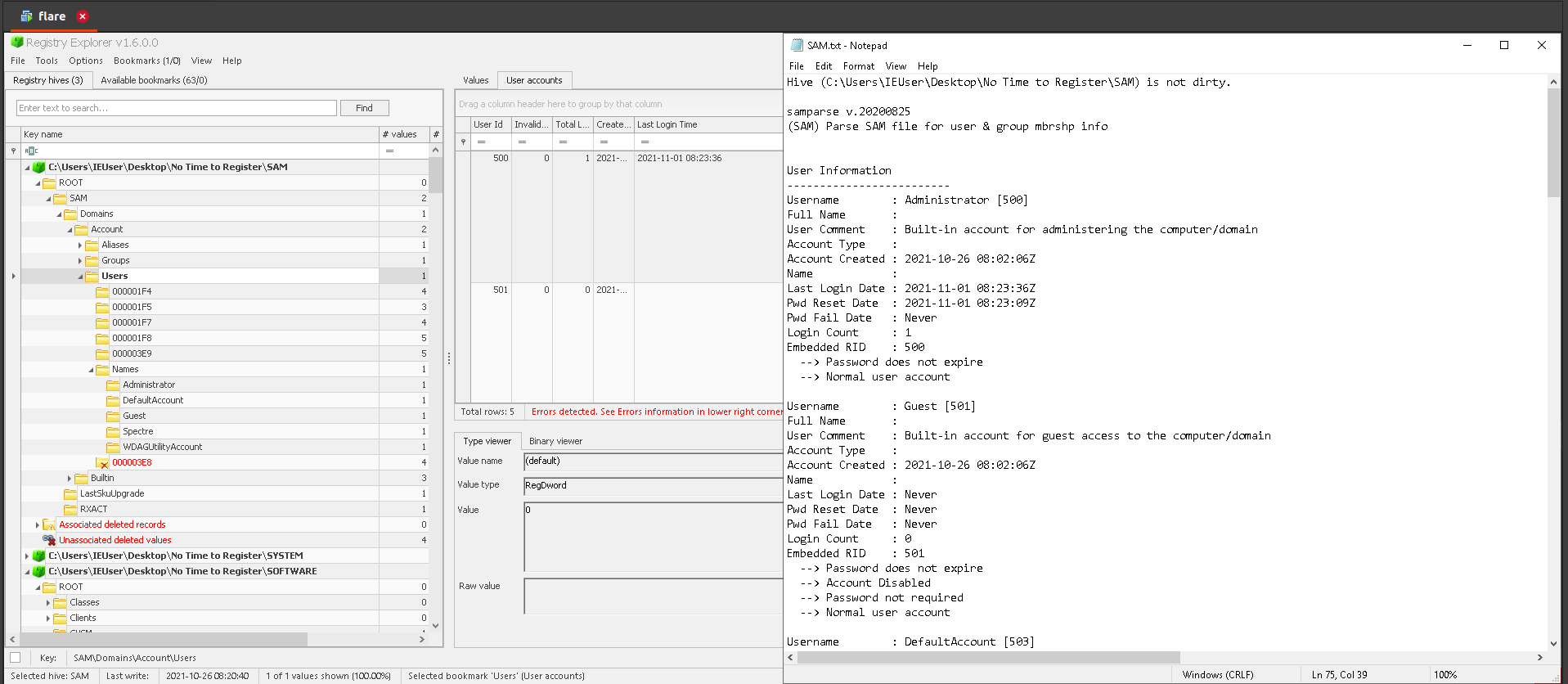 For USB artifacts, we will analyze registry hives with USB FORENSICS TRACKER and USBDeview.
For USB artifacts, we will analyze registry hives with USB FORENSICS TRACKER and USBDeview.
USB FORENSICS TRACKER: Click on the windows icon in the toolbar and select the folder which contains registry hives.
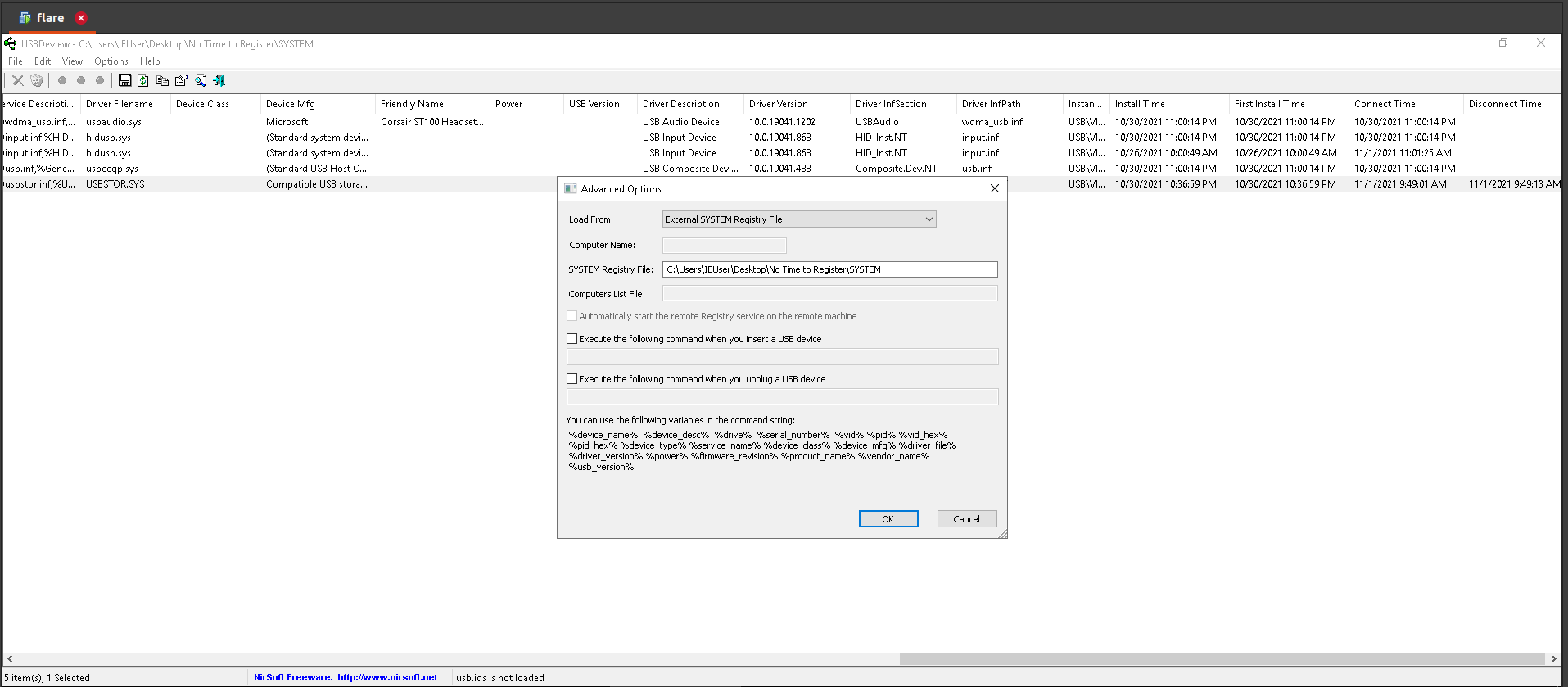
 USBDeview: Load the system hive from Options menu => Advanced Options
USBDeview: Load the system hive from Options menu => Advanced Options
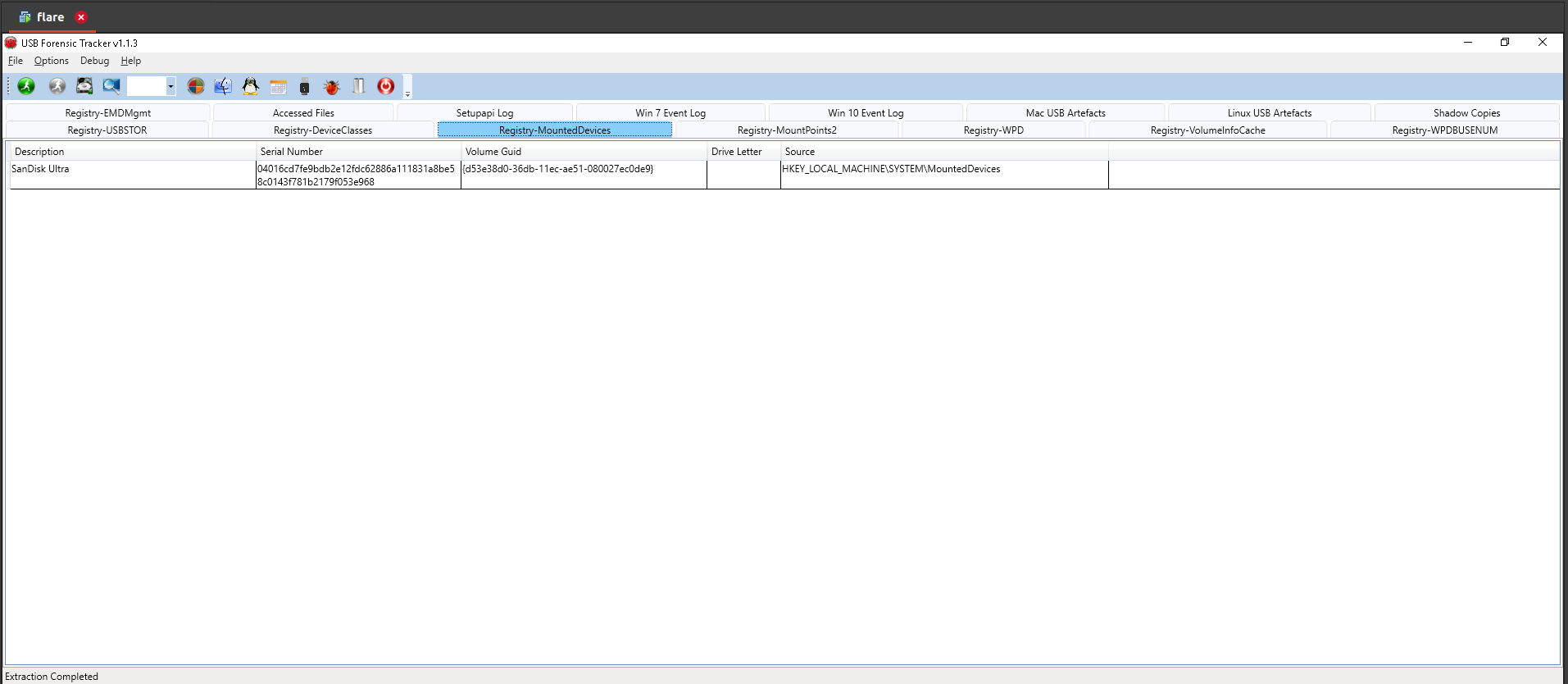
 7.Name of USB attached to the machine
7.Name of USB attached to the machine
Answer: 3v1L_Dr1v3
 8.Letter assigned to USB attached to the machine
8.Letter assigned to USB attached to the machine
Answer: E
 9.Serial number of USB attached to the machine
9.Serial number of USB attached to the machine
Answer: 04016cd7fe9bdb2e12fdc62886a111831a8be58c0143f781b2179f053e968
 10.Timestamp of first connection of USB to the machine. (Use format HH:MM:SS MM/DD/YYYY)
10.Timestamp of first connection of USB to the machine. (Use format HH:MM:SS MM/DD/YYYY)
Answer: First install time = 10/30/2021 10:36:59 PM
11.Timestamp of last connection of USB to the machine. (Use format HH:MM:SS MM/DD/YYYY)
Answer: Connect time = 11/1/2021 9:49:01 AM
12.Timestamp of last write to USB attached to the machine. (Use format HH:MM:SS MM/DD/YYYY)
Answer: Disconnect time = 11/1/2021 9:49:13 AM
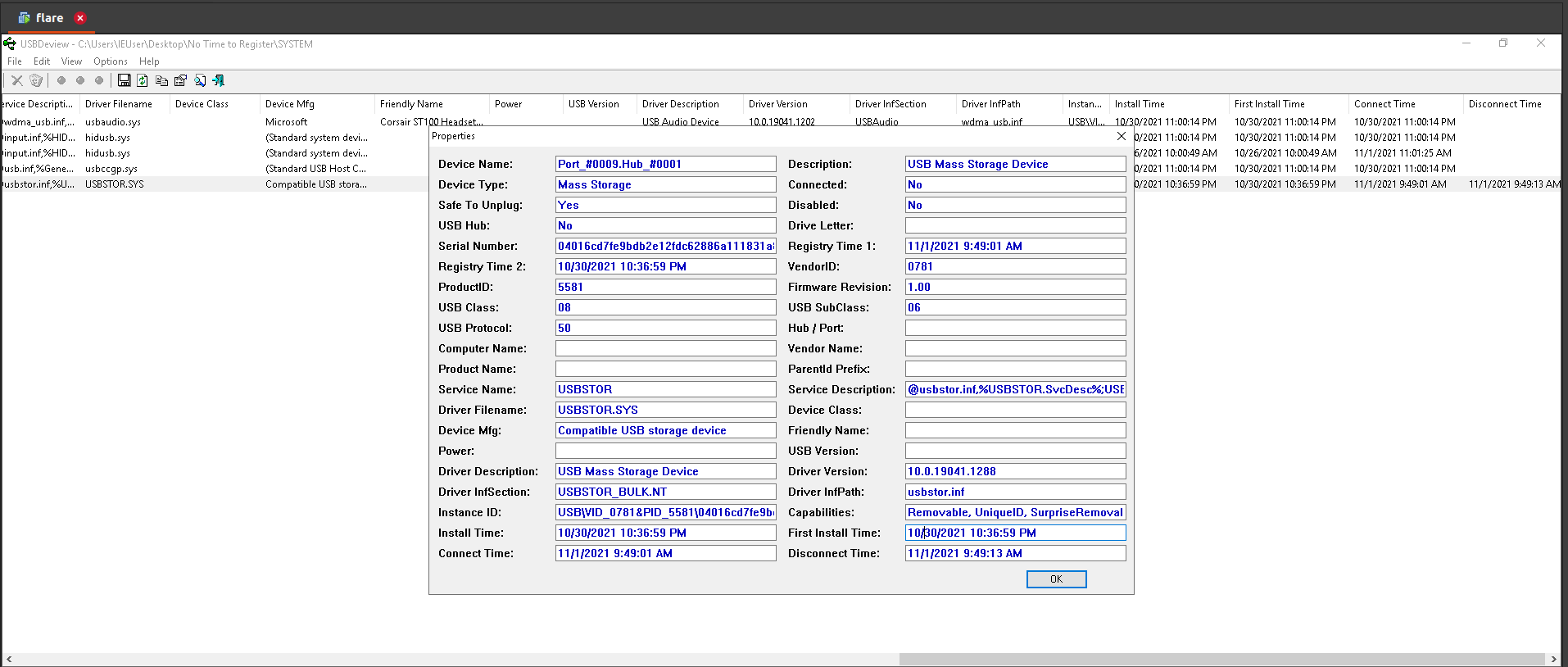 13.GUID of USB attached to the machine
13.GUID of USB attached to the machine
Answer: d53e38d0-36db-11ec-ae51-080027ec0de9
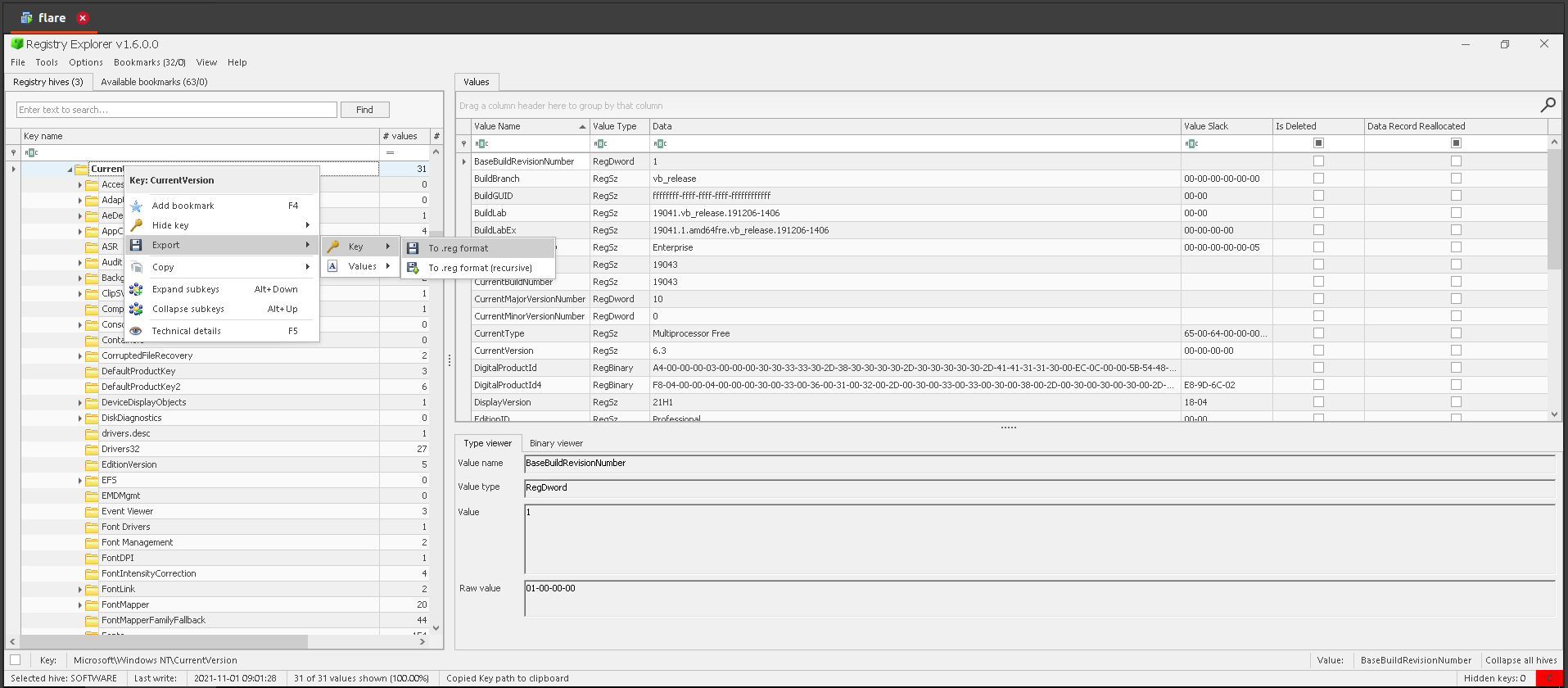
 14.Windows Activation Key
14.Windows Activation Key
For this question, load SYSTEM hive in Registry explorer and browse to SOFTWARE:Microsoft\Windows NT\CurrentVersion. Export CurrentVersion key to reg format.
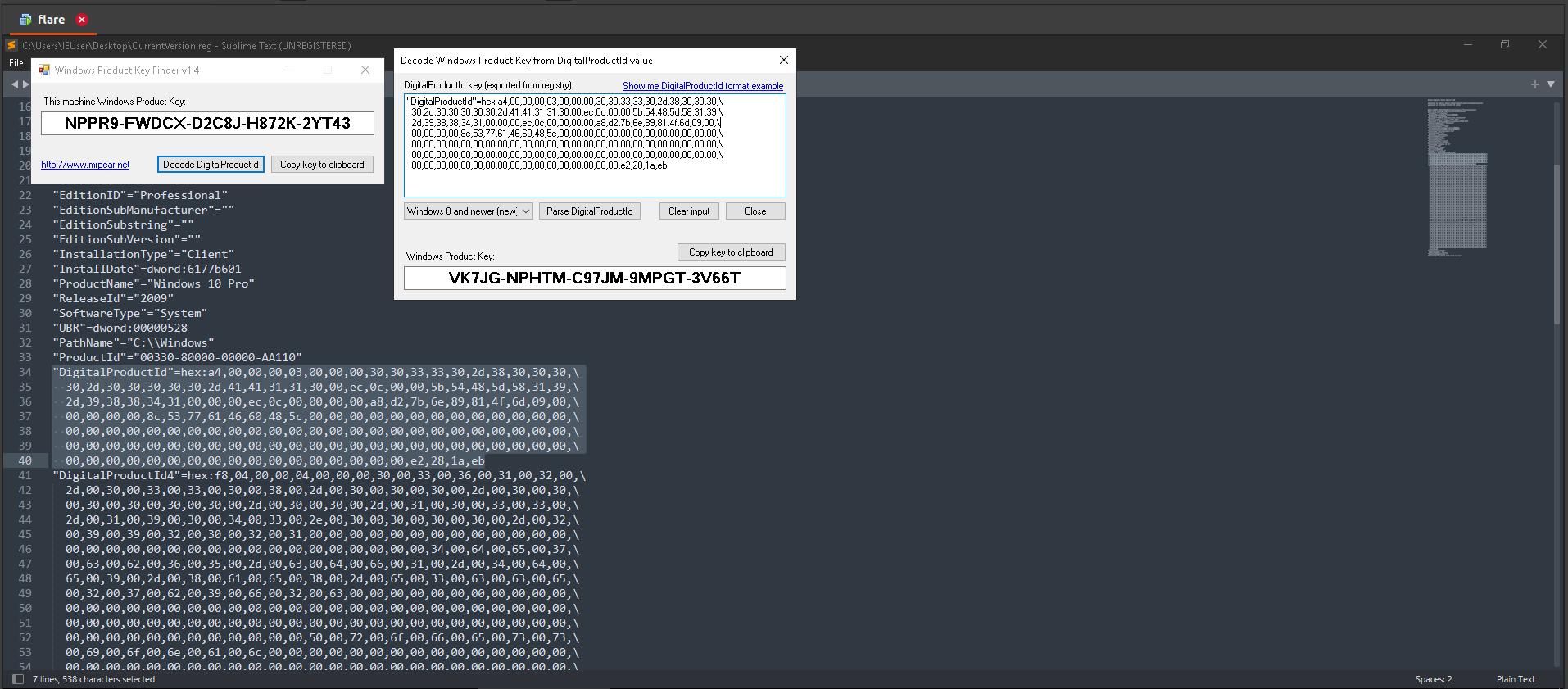
 Open the reg file in Notepad and copy the digitalproductid. Use WinProdKeyFinder to decode the digitalproductid and get the activation key.
Open the reg file in Notepad and copy the digitalproductid. Use WinProdKeyFinder to decode the digitalproductid and get the activation key.
Answer: VK7JG-NPHTM-C97JM-9MPGT-3V66T
 15.Windows Edition
15.Windows Edition
a. Registry Explorer: check CurrentVersion (Windows NT) in the bookmarks menu or browse to SOFTWARE:Microsoft\Windows NT\CurrentVersion. Check ProductName.
b. RegRipper: search ProductName in the software hive report.txt generated by RegRipper.
Answer: Windows 10 pro
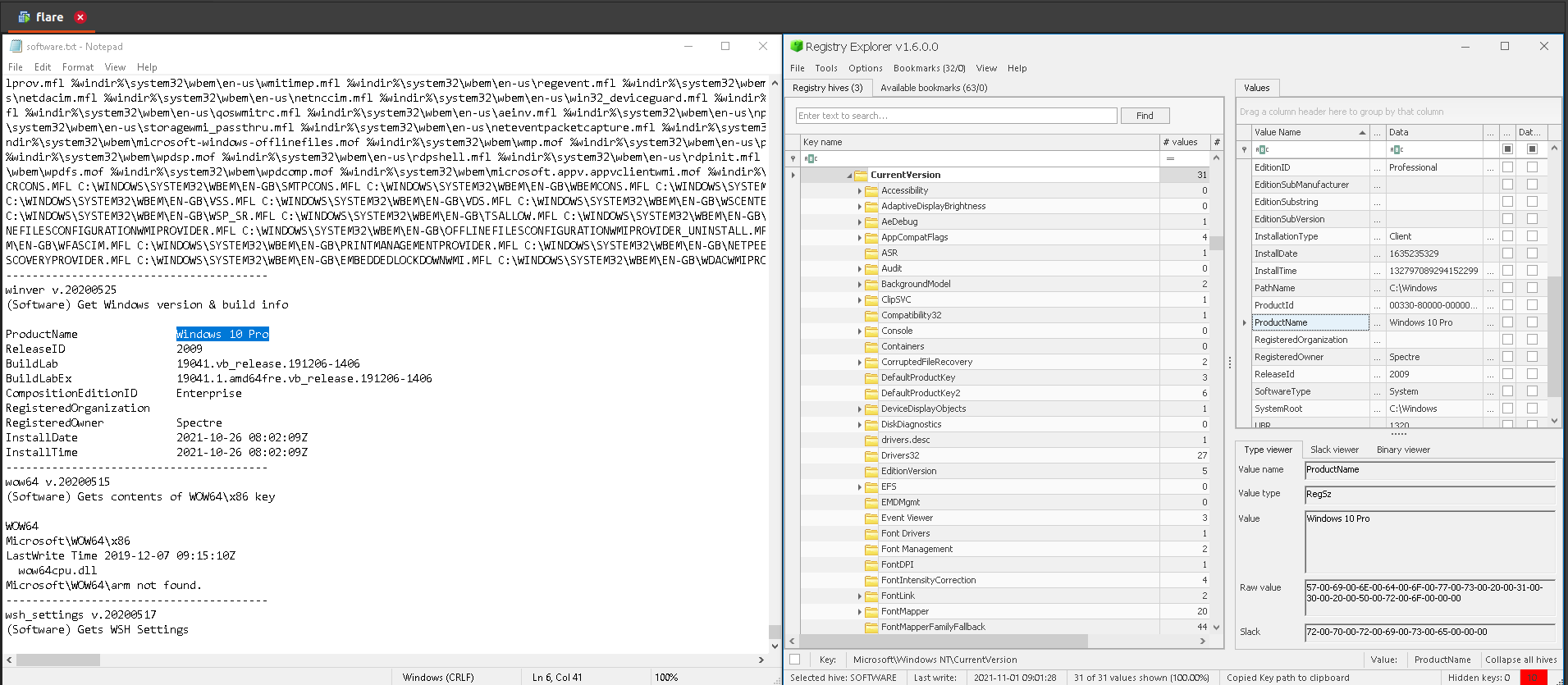 16.Windows Version
16.Windows Version
a. Registry Explorer: check CurrentVersion (Windows NT) in bookmarks menu or browse to SOFTWARE:Microsoft\Windows NT\CurrentVersion. Check DisplayVersion.
Answer: 21H1
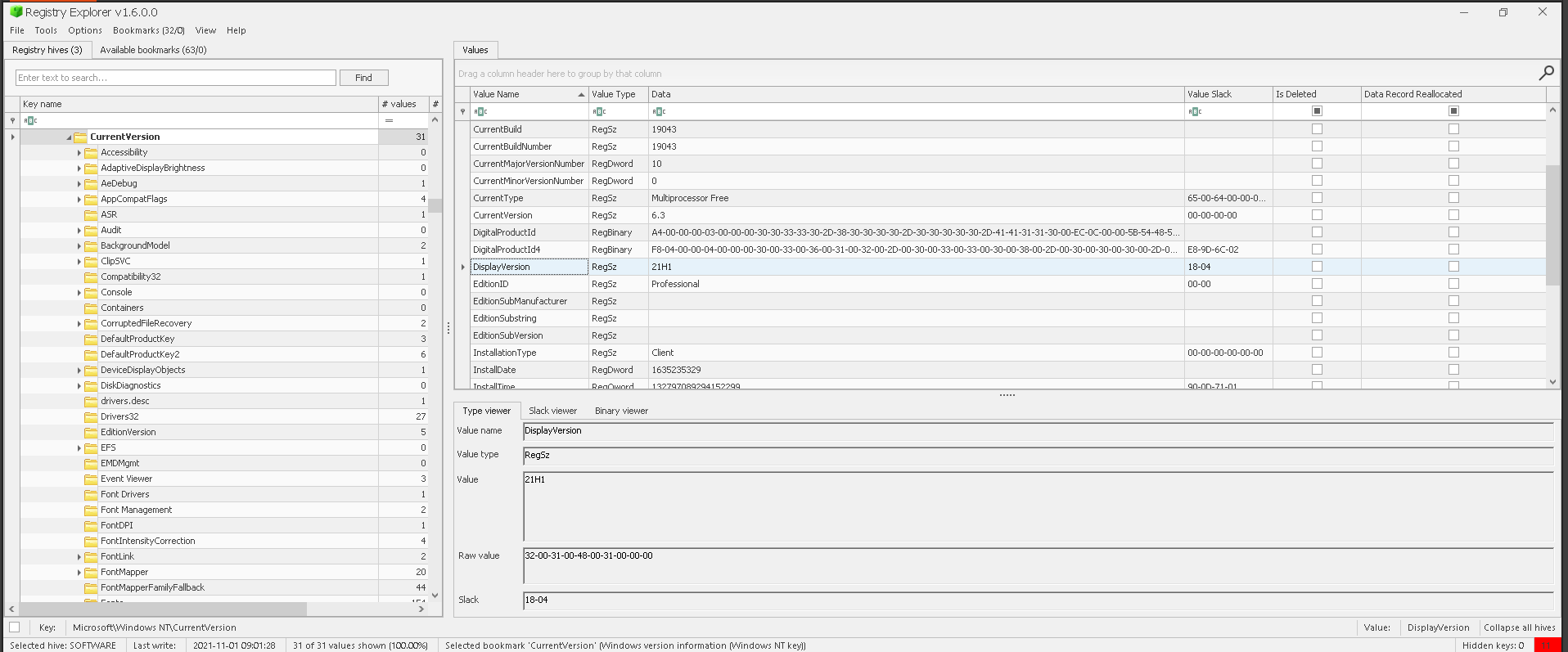 17.Windows Registered Owner
17.Windows Registered Owner
a. Registry Explorer: check CurrentVersion (Windows NT) in bookmarks menu or browse to SOFTWARE:Microsoft\Windows NT\CurrentVersion. Check RegisteredOwner.
b. RegRipper: search RegisteredOwner in the software hive report.txt generated by RegRipper.
Answer: Spectre
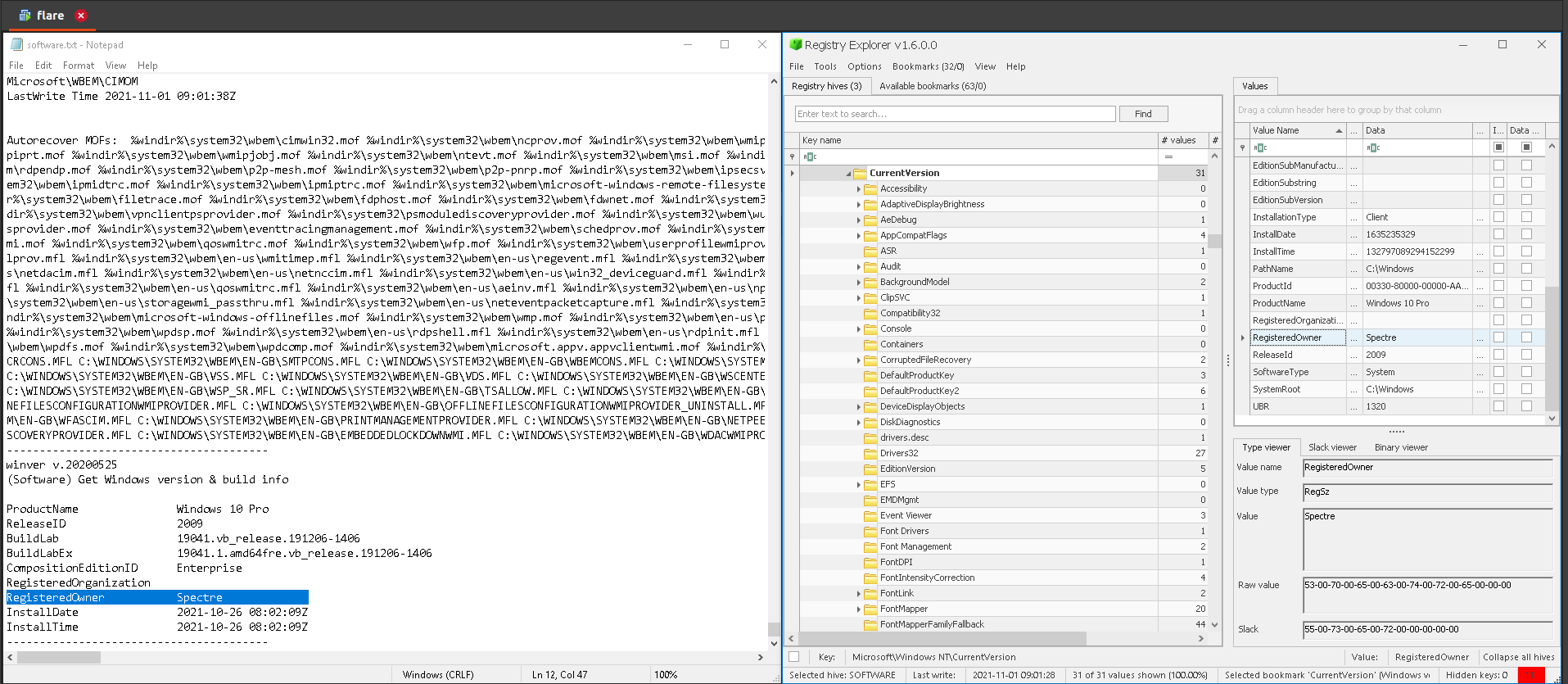 18.Windows Install Date. (Use format HH:MM:SS MM/DD/YYYY)
18.Windows Install Date. (Use format HH:MM:SS MM/DD/YYYY)
a. Registry Explorer: check CurrentVersion (Windows NT) in bookmarks menu or browse to SOFTWARE:Microsoft\Windows NT\CurrentVersion. Check Install time. Use Dcode to decode windows time.
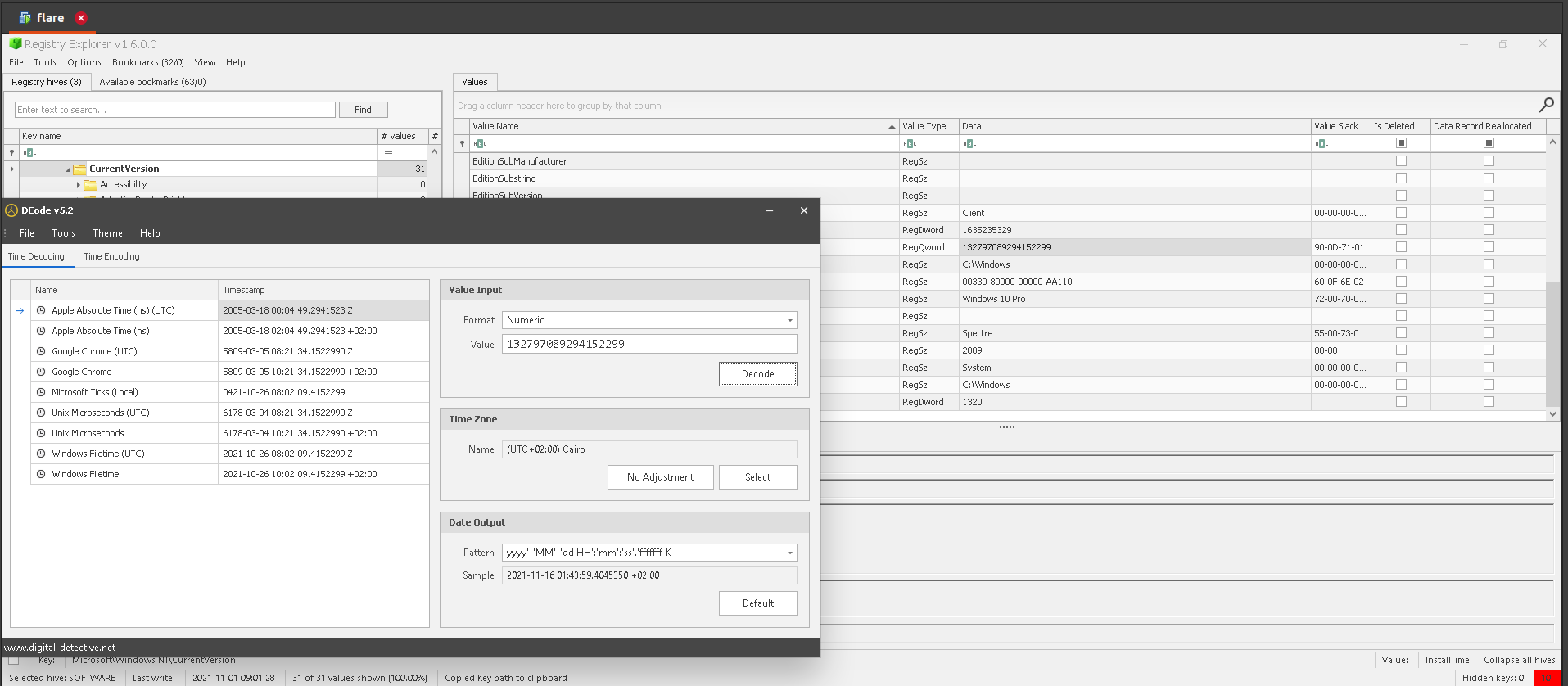 b. RegRipper: search InstallDate in the software hive report.txt generated by RegRipper.
b. RegRipper: search InstallDate in the software hive report.txt generated by RegRipper.
Answer: 2021-10-26 08:02:09Z