Description
Hidden deep within the dark web lies the flag you so need.
Author: Stephen Mondiguing, SecurityScorecard
(NOTE: the author used a slightly different flag format. Capitalize FLAG, e.g. FLAG{3x4mpl3_fl4g}, when submitting to CTFd.)
Tools
Walkthrough
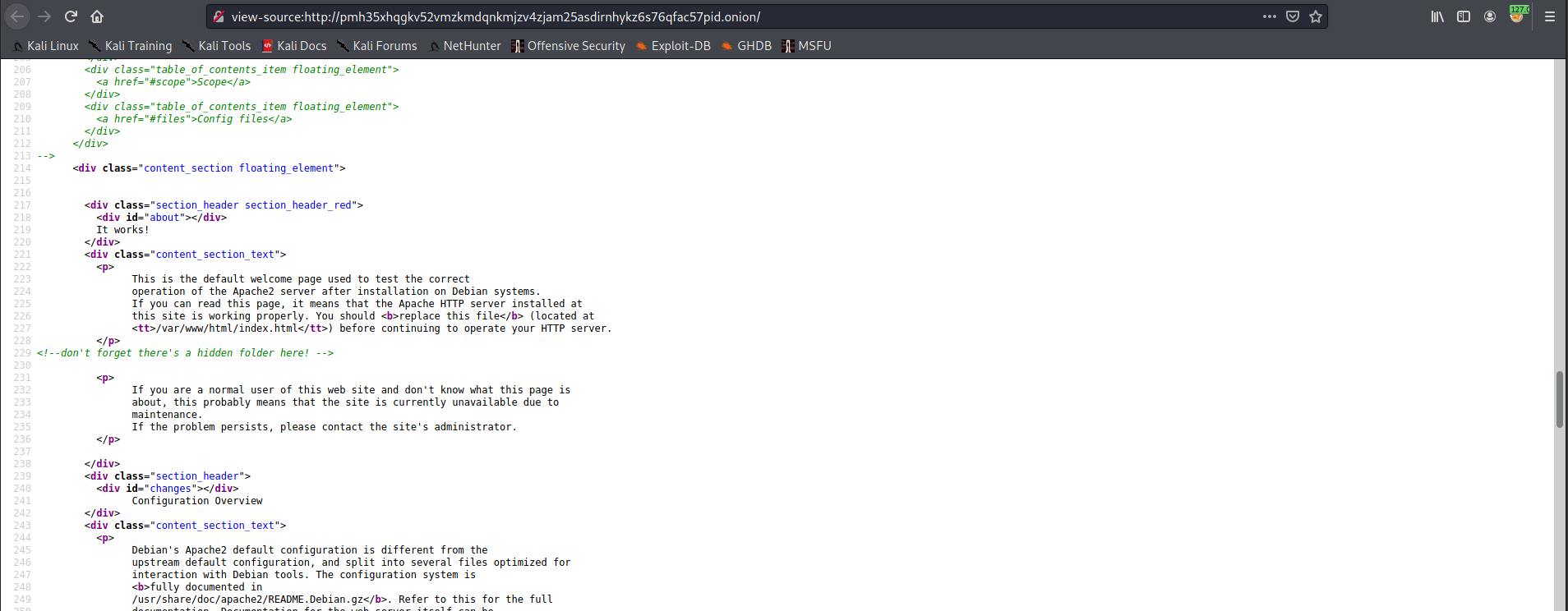
We were given an .onion website to examine. Check the website’s source code, and we found an HTML comment which states that there is a hidden folder on the website.
 Now we need to perform a directory bruteforce on the onion website. For that, we need to direct our bruteforce traffic through a tor proxy.
First, we need to install tor proxy using the following command
Now we need to perform a directory bruteforce on the onion website. For that, we need to direct our bruteforce traffic through a tor proxy.
First, we need to install tor proxy using the following command sudo apt install -y tor. After we run tor proxy, the output shows that the proxy is a SOCKS that runs on port 9050.
 After running tor proxy properly, we will use gobuster with common.txt wordlist from wfuzz to bruteforce the directories under the onion website.
Running gobuster
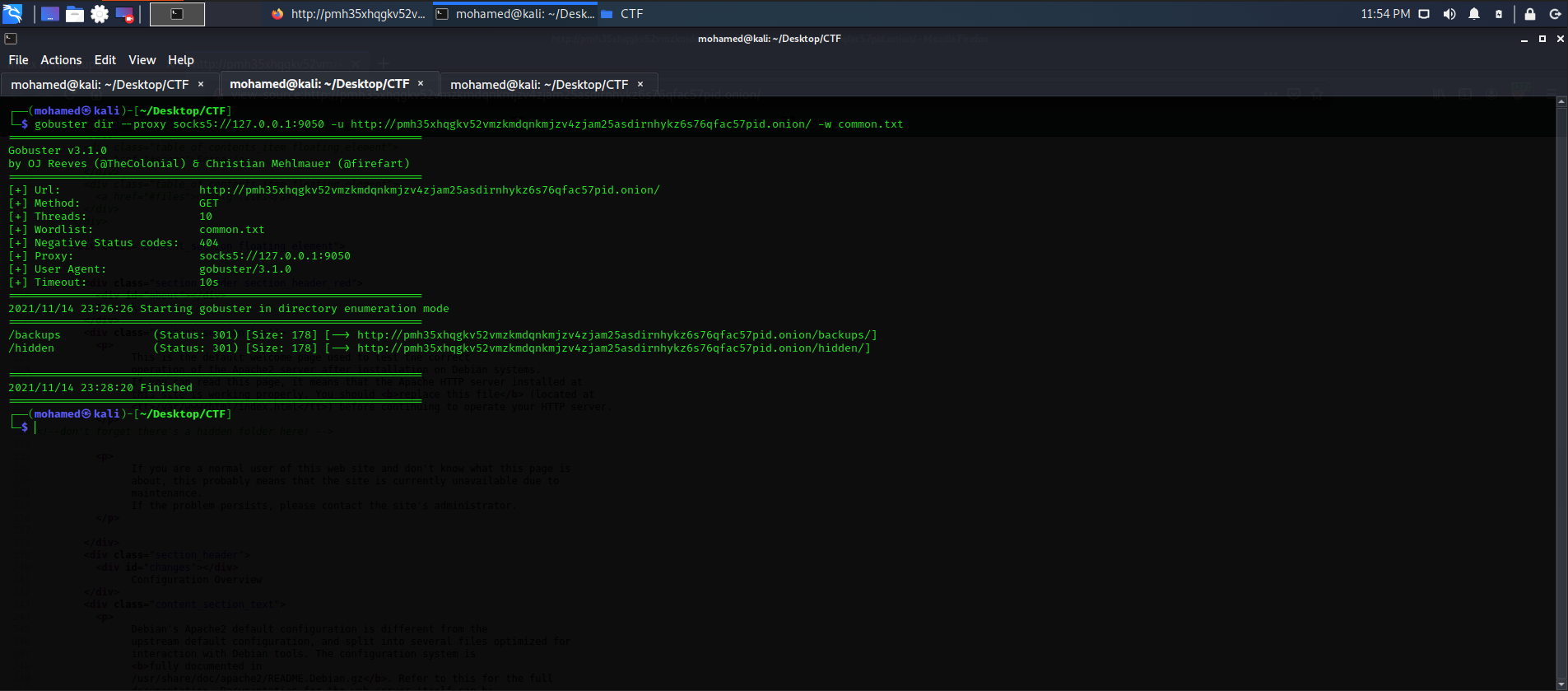
After running tor proxy properly, we will use gobuster with common.txt wordlist from wfuzz to bruteforce the directories under the onion website.
Running gobuster gobuster dir --proxy socks5://127.0.0.1:9050 -u http://pmh35xhqgkv52vmzkmdqnkmjzv4zjam25asdirnhykz6s76qfac57pid.onion/ -w common.txt gives us two directories, ‘backups’ and ‘hidden’
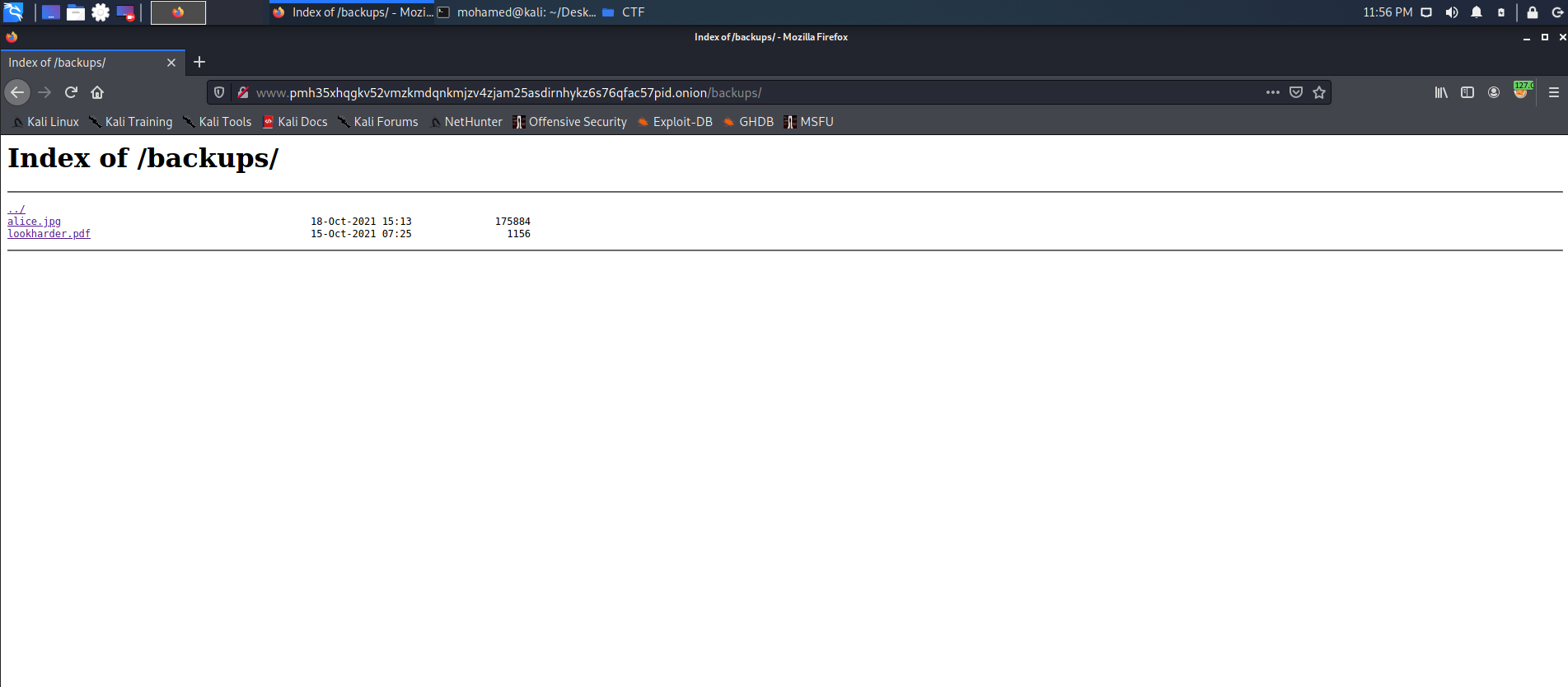
 Browsing the backups folder, we found two files, ‘alice.jpg’ and ‘lookharder.pdf’.
Browsing the backups folder, we found two files, ‘alice.jpg’ and ‘lookharder.pdf’.
 Checking the strings of the two files, we found a flag.txt in the pdf file.
Checking the strings of the two files, we found a flag.txt in the pdf file.
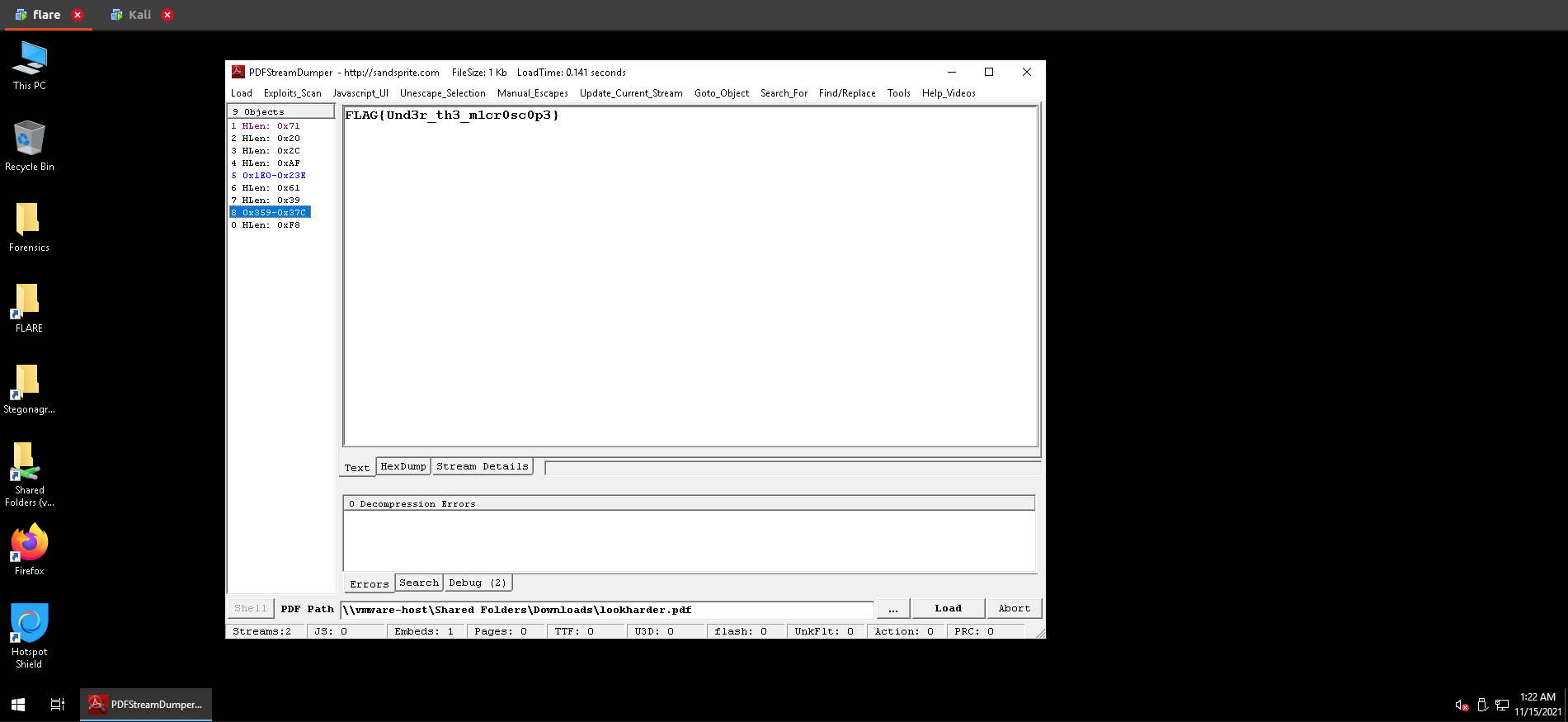
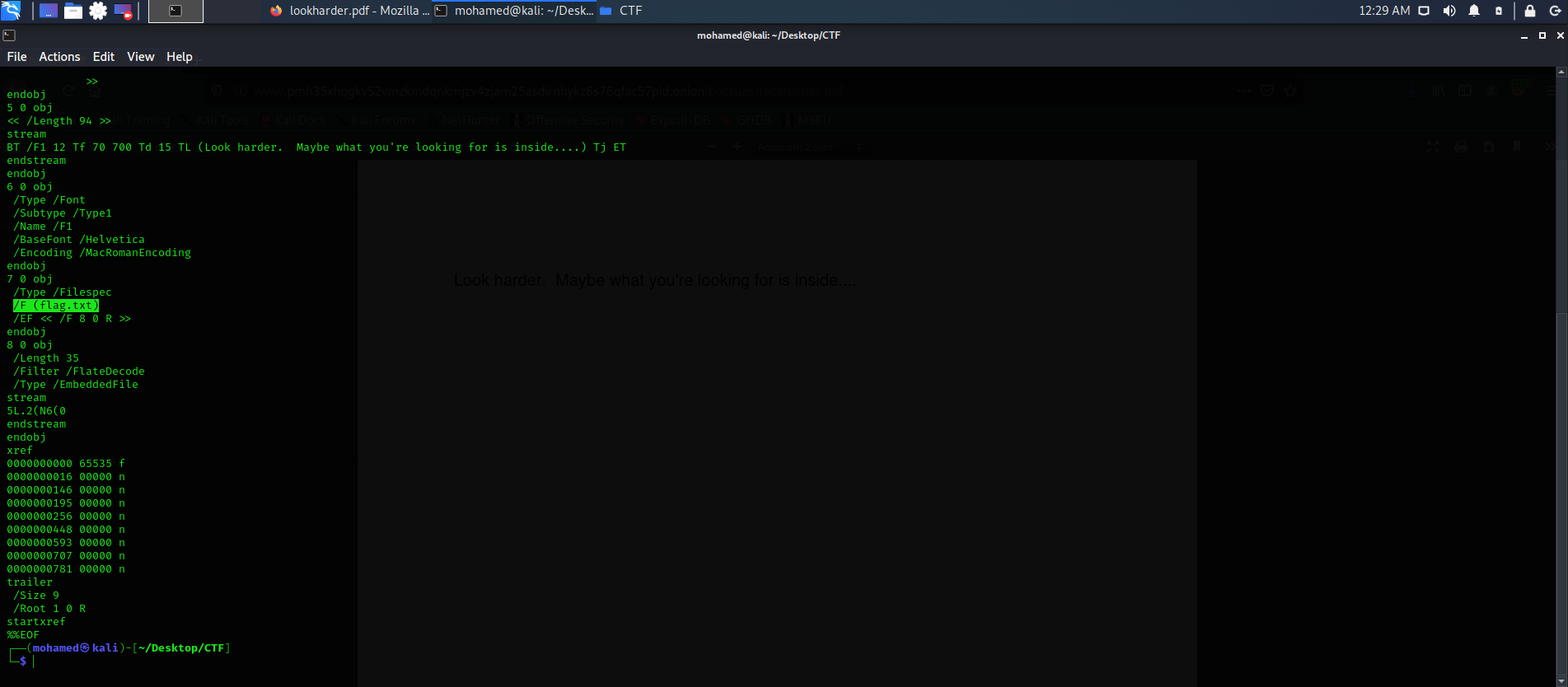 Loading the pdf file in pdfstreamdumper, we found the flag in one of the pdf streams.
Loading the pdf file in pdfstreamdumper, we found the flag in one of the pdf streams.